Overview
Risk Cognizance: Data Security Software | Cybersecurity Systems
Protecting sensitive data is paramount in today's digital age. Risk Cognizance provides robust data security software and comprehensive cybersecurity systems designed to help organizations safeguard their valuable information from evolving cyber threats. Our solutions empower you to implement strong data protection measures, maintain compliance with relevant regulations, and ensure business continuity.
Comprehensive Data Security and Cybersecurity Systems
Risk Cognizance understands that data security is a critical component of overall cybersecurity. Our integrated approach combines advanced data security software with comprehensive cybersecurity systems to provide a multi-layered defense against data breaches and other cyberattacks.
Simplify Regulatory Compliance with Risk Cognizance
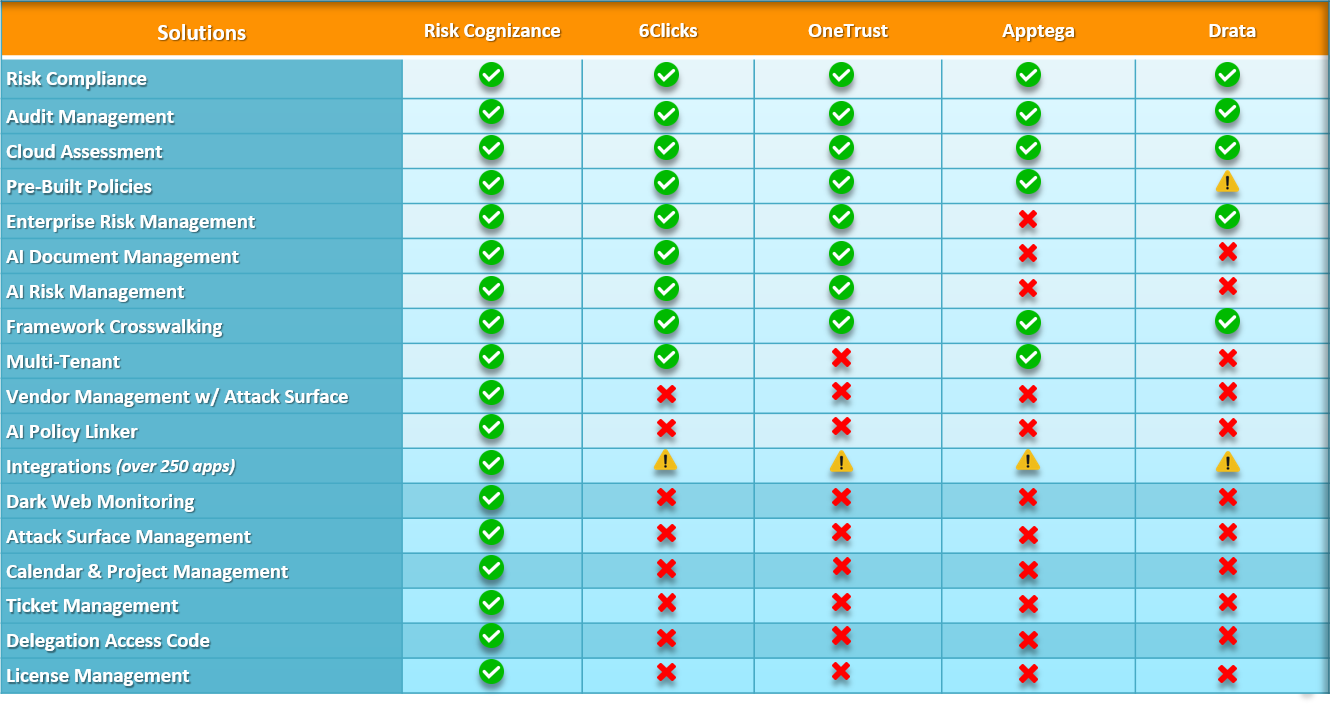
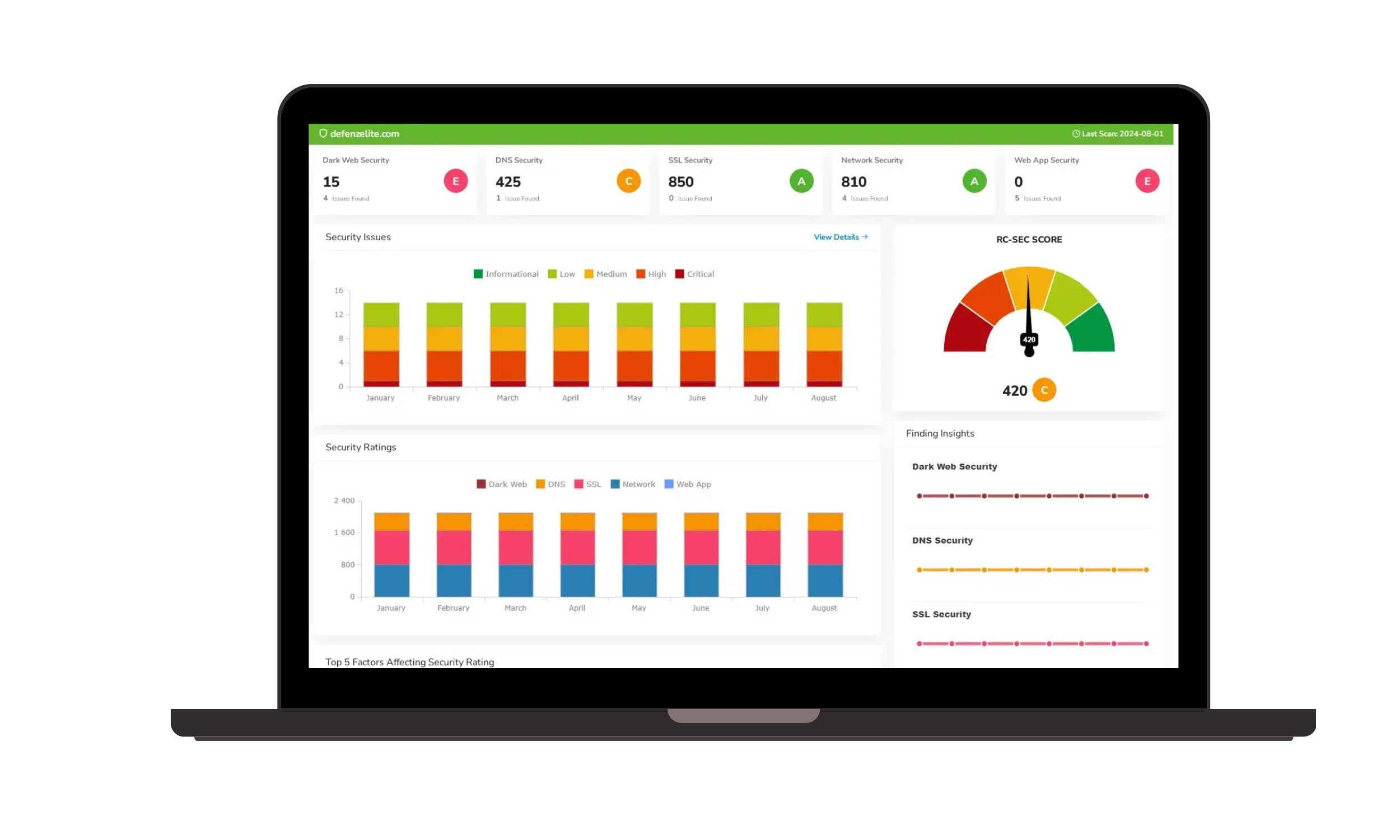
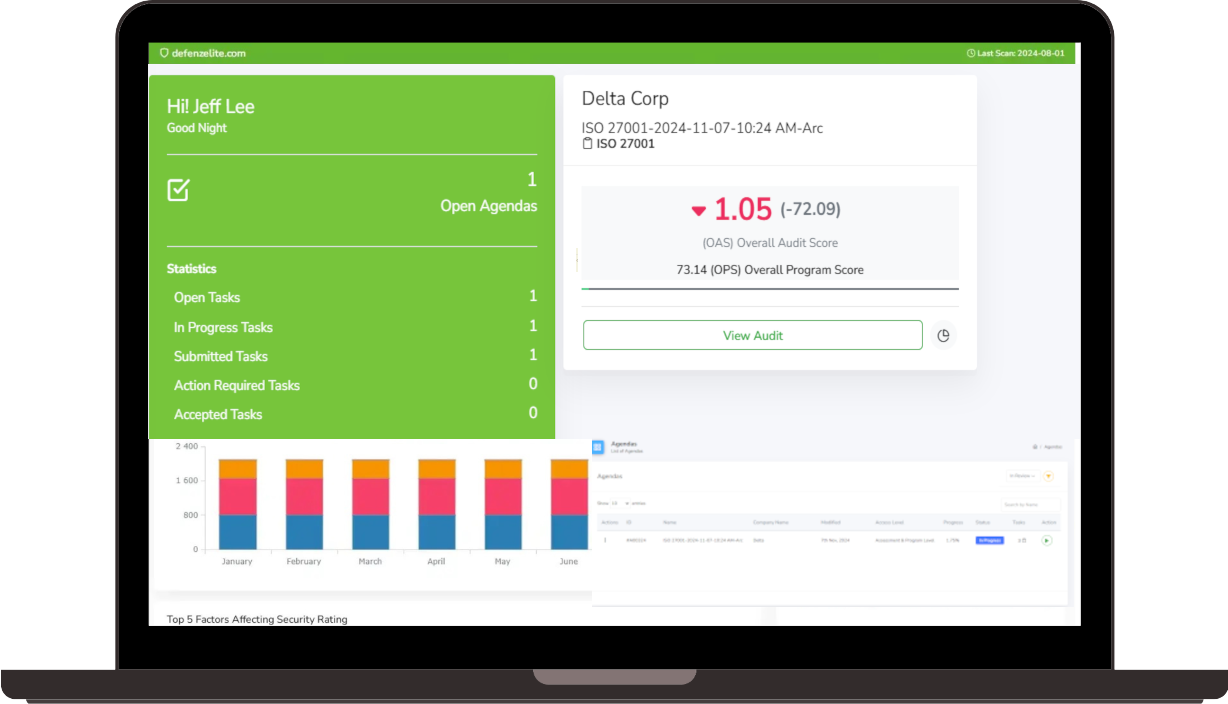
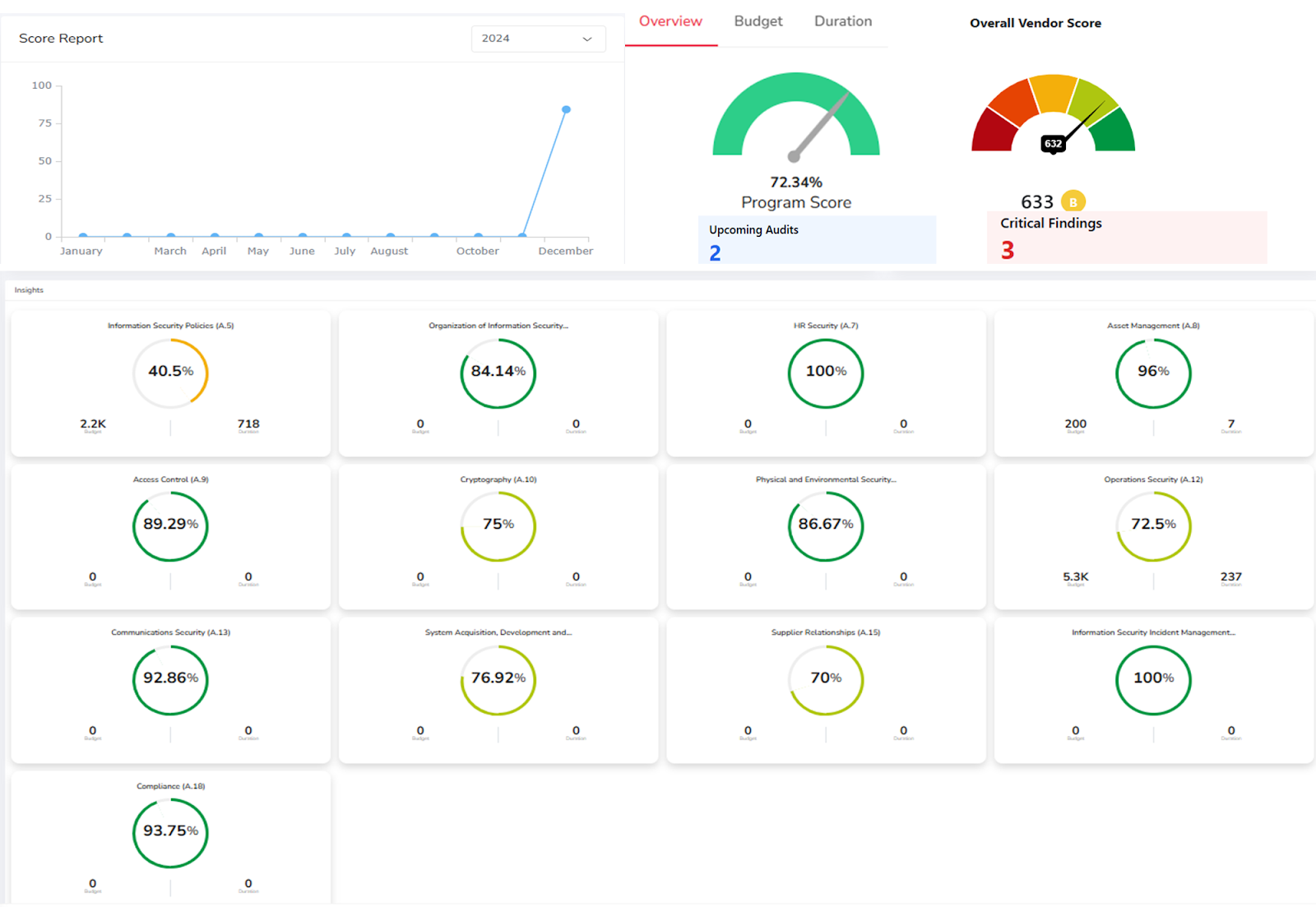
Choosing the right compliance management tool is crucial for navigating today's complex regulatory landscape. Risk Cognizance simplifies compliance management with 24/7 audit monitoring, dynamic dashboards and reports, integrated risk assessments, and ready-to-go templates. Our solution helps you satisfy a wide range of compliance requirements, including SOX, HIPAA, PCI DSS, FISMA, GLBA, GDPR, ISO 27001, and more.
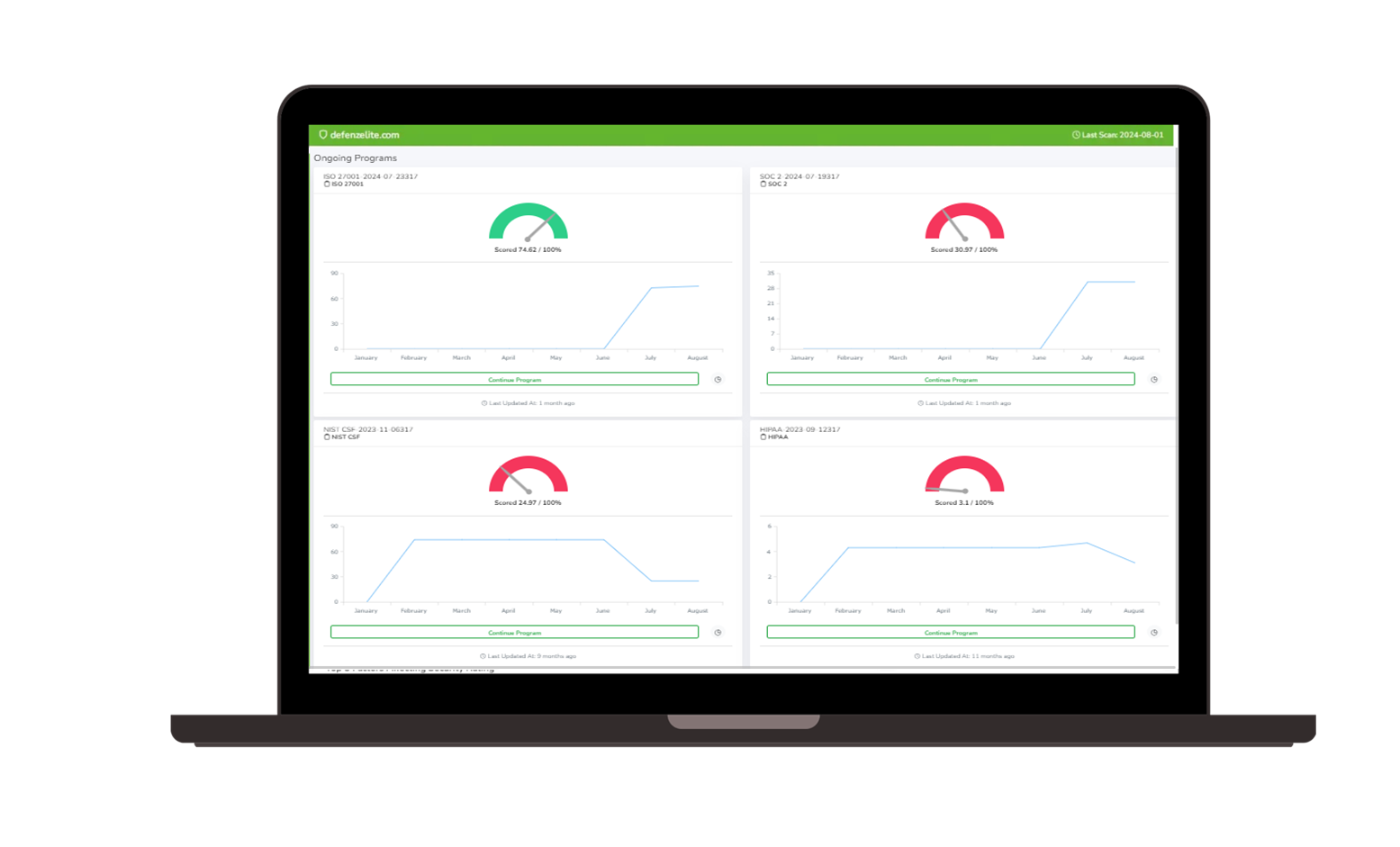
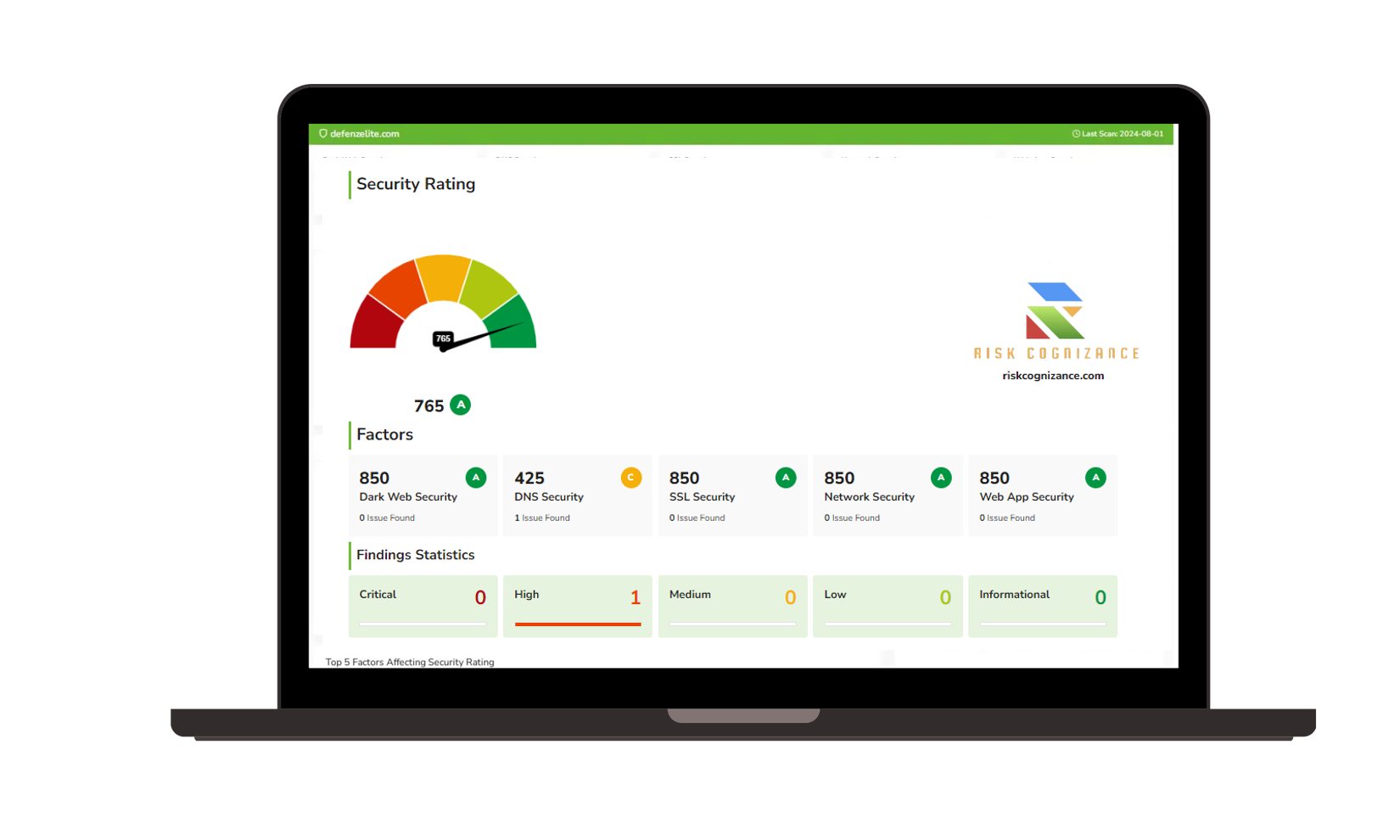
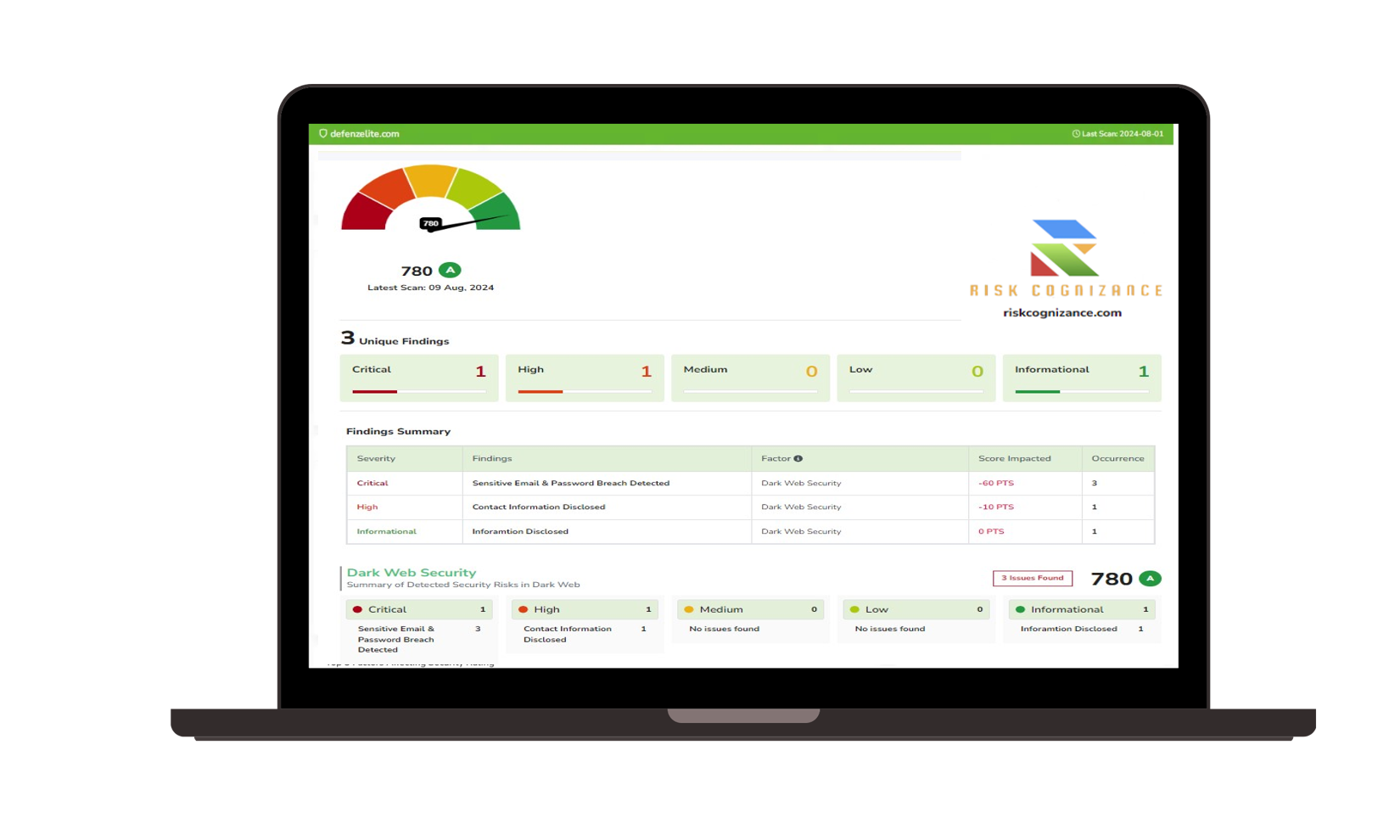
How Risk Cognizance Protects Your Data:
Our solutions address key data security and cybersecurity challenges through the following features and services:
- Data Loss Prevention (DLP):
- Data Discovery and Classification: Identify and classify sensitive data across your organization's systems and storage locations.
- Data Monitoring and Control: Monitor data movement and usage, preventing unauthorized access, transfer, or exfiltration.
- Endpoint DLP: Protect data on employee devices, preventing data leakage through USB drives, email, and other channels. This prevents sensitive data from leaving your control, whether intentionally or accidentally.
- Data Encryption:
- Data at Rest Encryption: Encrypt data stored on servers, databases, and other storage devices to protect it from unauthorized access.
- Data in Transit Encryption: Encrypt data transmitted across networks to prevent interception and eavesdropping. This ensures that even if data is intercepted, it is unreadable to unauthorized parties.
- Access Control and Identity Management:
- Role-Based Access Control (RBAC): Restrict access to sensitive data based on user roles and responsibilities.
- Multi-Factor Authentication (MFA): Require multiple forms of authentication to verify user identities and prevent unauthorized access.
- Privileged Access Management (PAM): Securely manage privileged accounts and prevent misuse of administrative privileges. This limits the potential damage from compromised accounts.
- Vulnerability Management (with a Focus on Data Security):
- Database Vulnerability Scanning: Identify security weaknesses in your databases that could lead to data breaches.
- Application Security Testing: Test applications for vulnerabilities that could expose sensitive data. This proactively identifies and addresses weaknesses that attackers could exploit to access data.
- Incident Response (with a Focus on Data Breaches):
- Data Breach Response Planning: Develop and implement plans to effectively respond to data breaches, minimizing damage and ensuring compliance with notification requirements.
- Forensic Investigation: Conduct thorough investigations to determine the root cause of data breaches and identify affected data. This is crucial for containing the breach, understanding the impact, and preventing future incidents.
- Compliance Management (for Data Privacy Regulations):
- GDPR, CCPA, HIPAA Compliance: Help you meet the requirements of various data privacy regulations.
- Data Mapping and Inventory: Maintain a comprehensive inventory of your data and its location. This is essential for demonstrating compliance and responding to data subject requests.
 |  |
 |  |
 |  |
Benefits of Using Risk Cognizance for Data Security and Cybersecurity:
- Reduced Risk of Data Breaches: Proactive data protection measures significantly reduce the likelihood and impact of data breaches.
- Enhanced Data Privacy: Ensure compliance with relevant data privacy regulations.
- Improved Security Posture: Strengthen your overall security posture through comprehensive cybersecurity systems.
- Faster Incident Response and Recovery: Minimize downtime and damage in the event of a data breach or other security incident.
- Increased Customer Trust: Demonstrate a strong commitment to data security and privacy, building trust with your customers.
Who Can Benefit from Risk Cognizance Data Security and Cybersecurity Solutions?
Risk Cognizance is suitable for organizations of all sizes and across various industries, especially those handling sensitive data, such as:
- Healthcare organizations
- Financial institutions
- Retail businesses
- Government agencies
Choose Risk Cognizance for Your Data Security and Cybersecurity Needs
Risk Cognizance provides the robust data security software and comprehensive cybersecurity systems you need to protect your valuable information and ensure business continuity. Contact us today to learn more and request a demo.
Request Callback
